LS-Auth integration with keycloak as IDP (OIDC)
Below are instructions to set up keycloak as an IDP for LSAuth using OIDC
Creating LSAuth Client on KeyCloak
-
Login to your keycloak Admin UI instance and select the realm you want to create the client under.
-
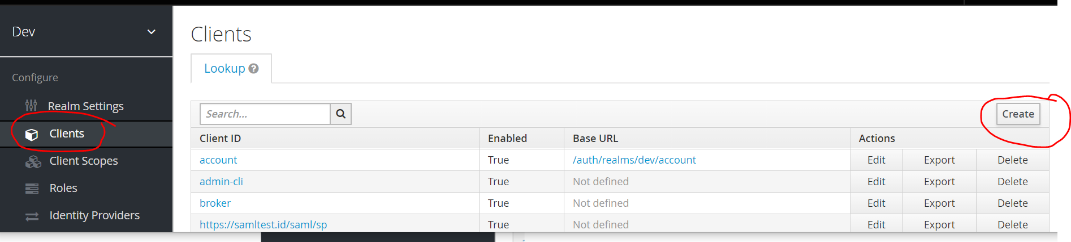
Navigate to clients from left nav and click on create (right corner)
-
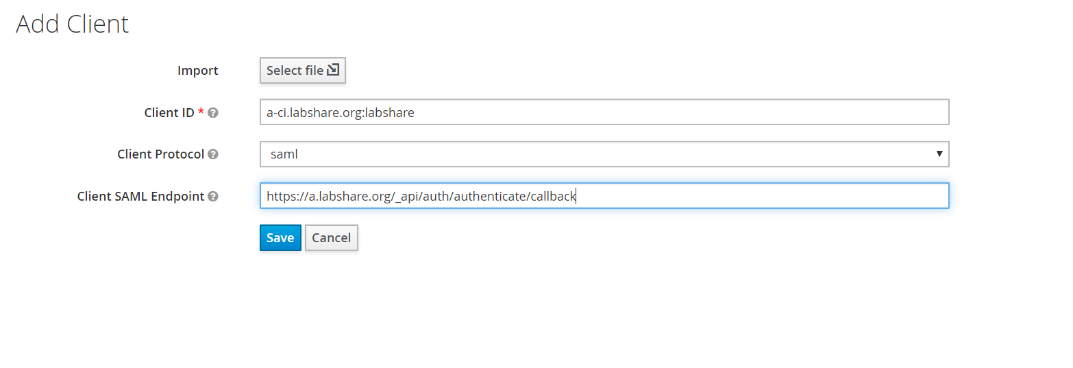
Enter the required information. ClientID is a unique string set for this client. Client protocol needs to be OIDC and Root URL needs to be LSAuth call back URL (Refer to LS-Auth: Quick Links )
-
Click Save
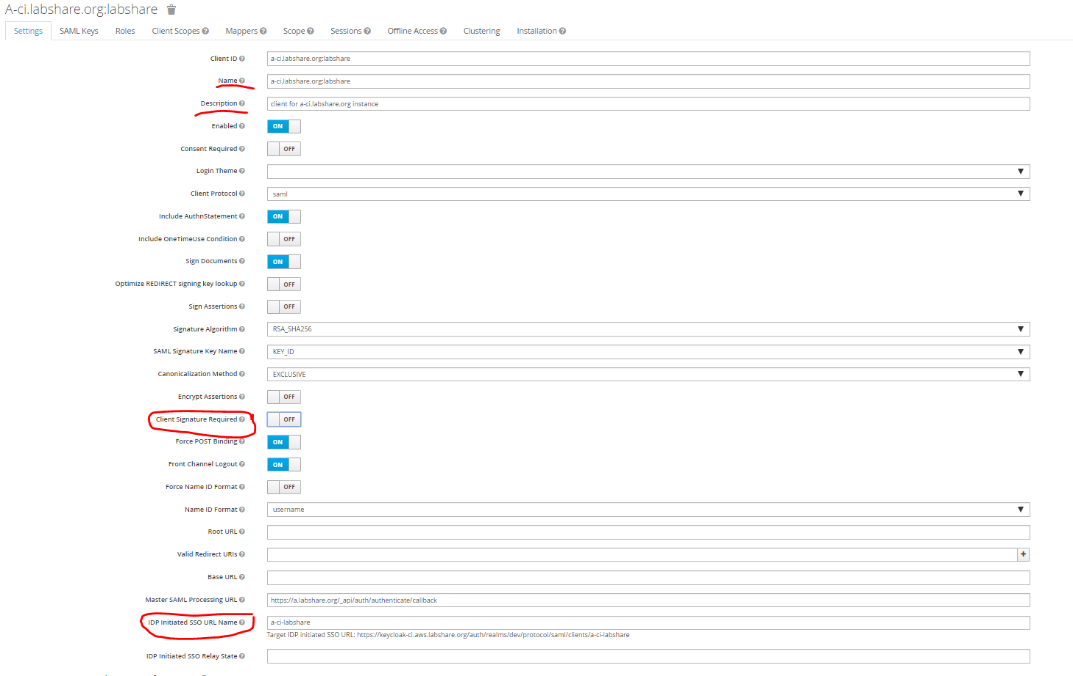
- On the next screen enter Name and Description for the client. Set Access Type to public, enable Standard flow, disable implicit flow.
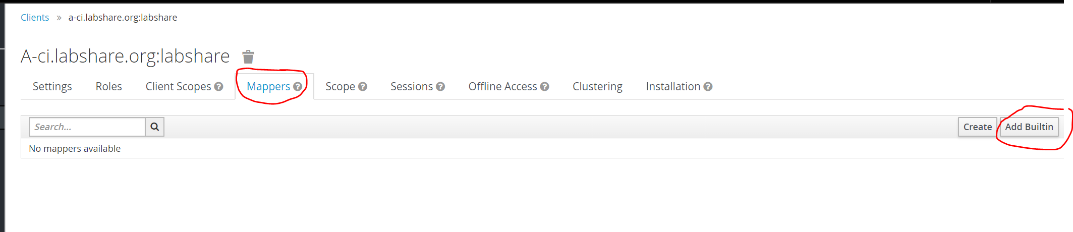
- Map the OIDC claims using the mappers tab
- Note down the clientID and Discovery URL
.well-known/openid-configuration
(Eg:
https://keycloak-ci.aws.labshare.org/auth/realms/dev/.well-known/openid-configuration)
Create an Identity Provider Configuration in LSAuth
-
Log into the LS Auth console for and select the tenant that you will use.
-
Select “Providers” in the left nav menu and click the “Add New” button.
-
Select Provider Type “OIDC”
-
Enter the below details (You will need to use the details you noted above from Keycloak above )
Discovery URL : Keycloak Discovery URL eg:
https://keycloak-ci.aws.labshare.org/auth/realms/dev/.well-known/openid-configuration
Client ID : Keycloak client ID
(As we are using this only for authentication we are doing a public flow and doesn't need client secret)
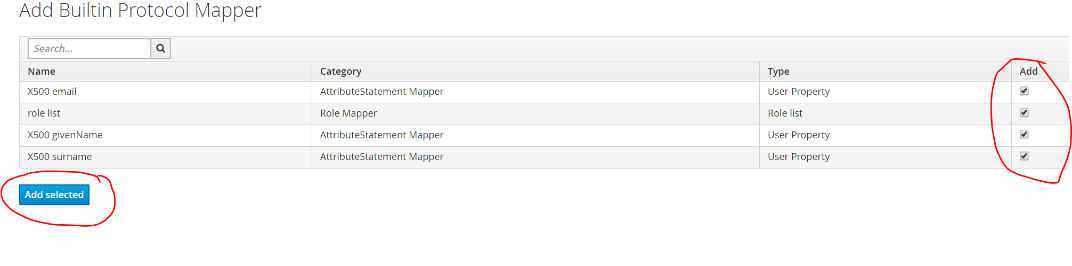
- Save the provider