LS-Auth integration with google as IDP (SAML)
Below are instructions to set up google as an IDP for LSAuth using SAML.
Creating application on Google
- Sign in to your Google admin console.
Sign in using your administrator account (does not end in \@gmail.com).
- From the Admin console Home page, go to Apps
SAML apps.
-
Click Add at bottom right.
-
Click Set up my own custom app.
- The Google IDP Information window opens and the SSO URL and Entity ID fields automatically populate.
-
Copy the SSO URL and Entity ID and download the Certificate.These will be needed for the Service provider setup.
-
Click Next.
-
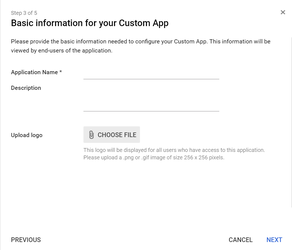
In the Basic information window, add an application name and description.
-
(Optional) Upload a PNG or GIF file to serve as an icon for your custom app. The icon image should be 256 pixels square.
-
Click Next.
-
In the Service Provider Details window, enter an ACS URL and Entity ID. Entity Id needs to be unique string defined by LSAuth (suggested format would be LSAuth env base url:tenant:saml:IDP name:google <<LSAuth env base url:tenant:saml:IDP name>>), ACS URL for LSAuth can be found at https://labshare.atlassian.net/wiki/spaces/LA/pages/682000386/LS-Auth+Quick+Links#Callback%2FACS-and-Federated-Logout-URLs
-
The default Name ID is the primary email.
-
Click Next.
-
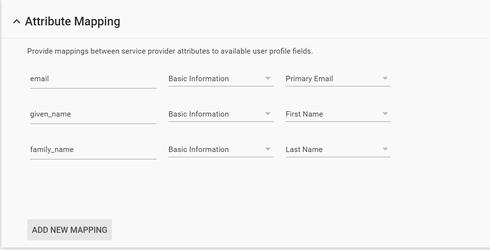
Click Add new mapping and enter a new name for the attribute you want to map.
-
In the drop-down list, select the Category and User attributes to map the attribute from the Google profile.
Note: You cannot use Employee ID for attribute mapping. -
Click Finish.
-
To turn on the SSO for the newly created SAML app, Select your new SAML app on the admin page
-
To turn on or off a service for everyone in your organization, click On for everyone , and then click Save.
NOTE:
Ensure that the email addresses your users use to sign in to the SAML app match the email addresses they use to sign in to your Google domain. Changes typically take effect in minutes, but can take up to 24 hours. For details, see How changes propagate to Google services.
Create an Identity Provider Configuration in LSAuth
-
Log into the LS Auth console for and select the tenant that you will use.
-
Select “Providers” in the left nav menu and click the “Add New” button.
-
Select Provider Type “SAML2”
-
Enter the below details (You will need to use the details you noted from Google IDP configuration steps above)
IDP URL (SSO URL copied from above): https://accounts.google.com/o/saml2/idp?idpid=sdsfdfasdfsa
Logout URL (IDP Logout URL): https://accounts.google.com/logout
Realm has to match the SP Entity ID provided in the Single sign on configuration in SAML application created above.(suggested format would be LSAuth env base url:tenant:saml:IDP name:google <<LSAuth env base url:tenant:saml:IDP name>>)
Signing Cert: Base64 IDP certificate you download above
Use “User Profile Script” editor to set claim mappings. Copy the below
script into the “User profile Script” block
Note: Additional claims mapping options are also available in the
application configuration.
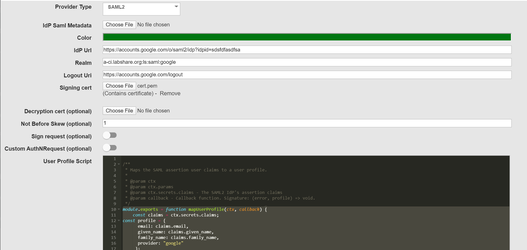
module.exports = function mapUserProfile(ctx, callback) {
const claims = ctx.secrets.claims;
const profile = {
email: claims.email,
given_name: claims.given_name,
family_name: claims.family_name,
provider: "google"
};
callback(null, profile);
}
NOTE: When you are logging in for the first time, Azure will ask for user confirmation on access request .