LS-Auth integration with azure as IDP (OAuth)
Below are instructions to set up azure as an IDP for LSAuth using OpenID Connect (OIDC).
Create an enterprise application configuration in Azure
-
Open a browser and navigate to the App registrations in Azure AD Portal. (Login required)
-
Click + New registration from the current blade content.
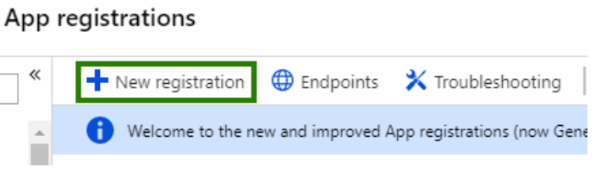
- On the Register an application page, specify the following values:
Name = Labshare Auth OIDC - a.labshare.org (Unique name per application)
Supported account types = <choose the value that applies to your needs>
Redirect URI = Web : https://localhost:8080 (This should be your SP callback URL)
Note: The Redirect URI value can be changed later and can also be pointed at a URI that isn’t actually hosted.
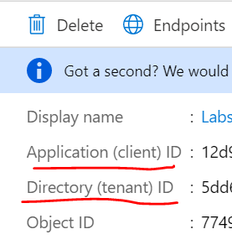
- Click “Register” button to register the application. After the app is created you will be directed to the application Overview page. On this page, copy the Application (client) ID and Directory (tenant) ID as you will need them later.
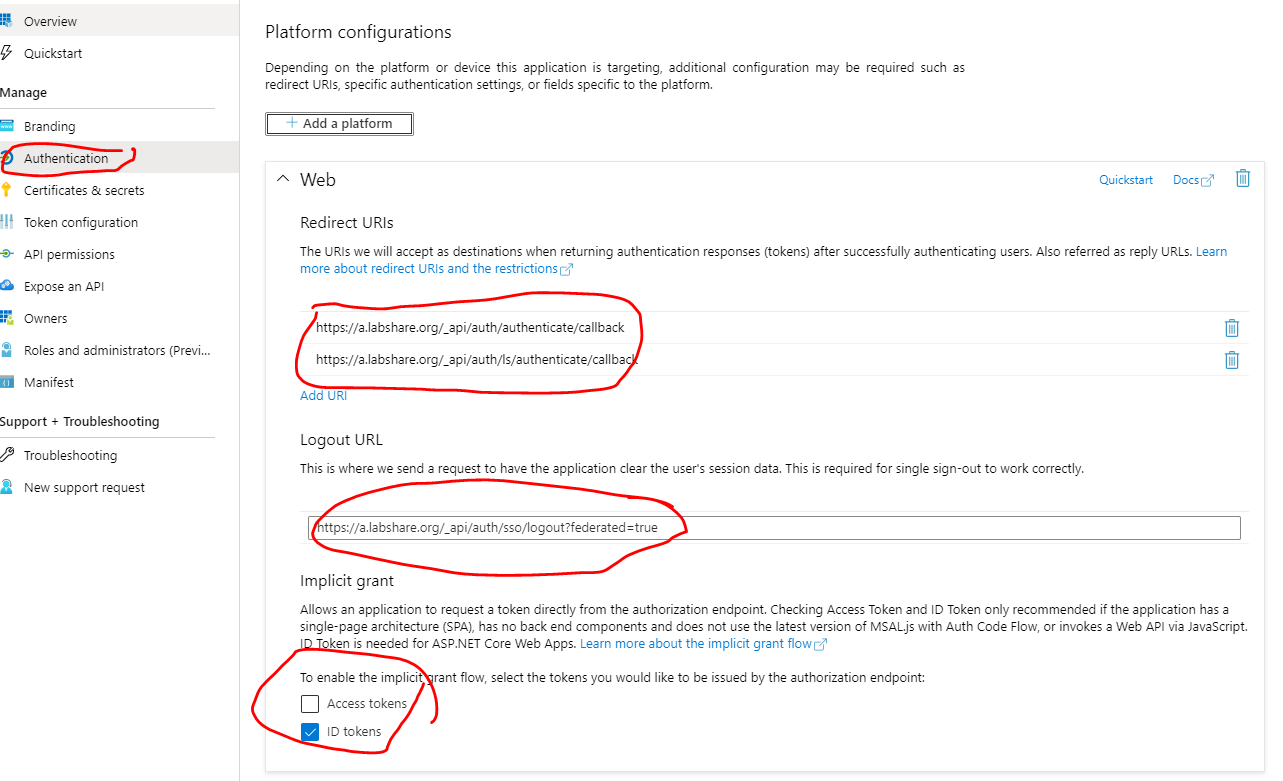
- Select Authentication from the current blade navigation panel. Update callback URLs and logout URL as per the Client / Service provider. Also ensure that ID Token is selected for Implicit grant flow.
Create the Identity Provider Configuration in LSAuth
-
Log into the LS Auth console and select the tenant that you will use.
-
Select “Providers” in the left nav menu and click the “Add New” button.
<!-- -->
-
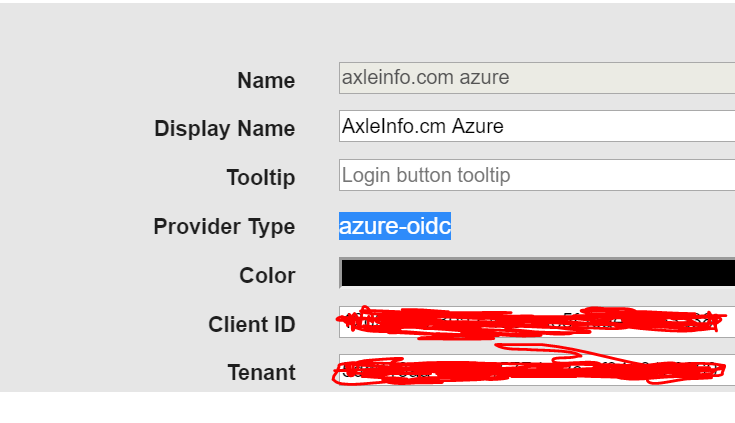
Create a new Provider of type azure-oidc
-
Enter the Client ID and Tenant ID (Copied from the Application configuration on Azure)
NOTE: When you are logging in for the first time, Azure will ask for user confirmation on access request .