LS-Auth integration with keycloak as IDP (SAML)
Below are instructions to set up keycloak as an IDP for LSAuth using SAML.
Creating LSAuth Client on KeyCloak (Service provider)
-
Login to your keycloak Admin UI instance and select the realm you want to create the client under.
-
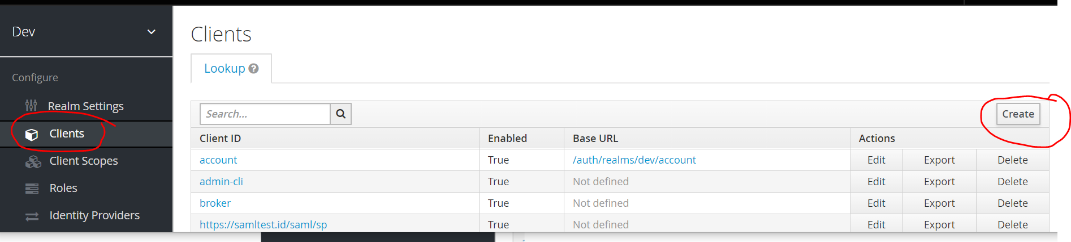
Navigate to clients from left nav and click on create (right corner)
-
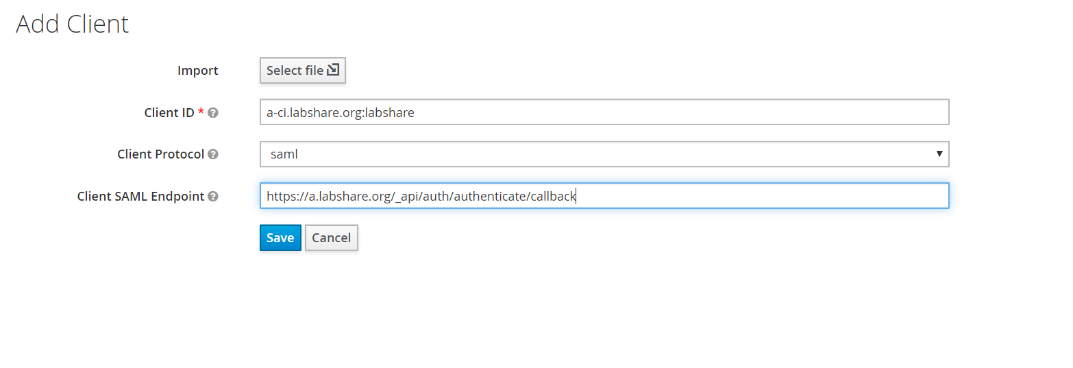
Enter the required information. ClientID is a unique string set for this client. Client protocol needs to be SAML and SAML endpoint needs to be LSAuth call back URL (Refer to LS-Auth: Quick Links )
-
Click Save
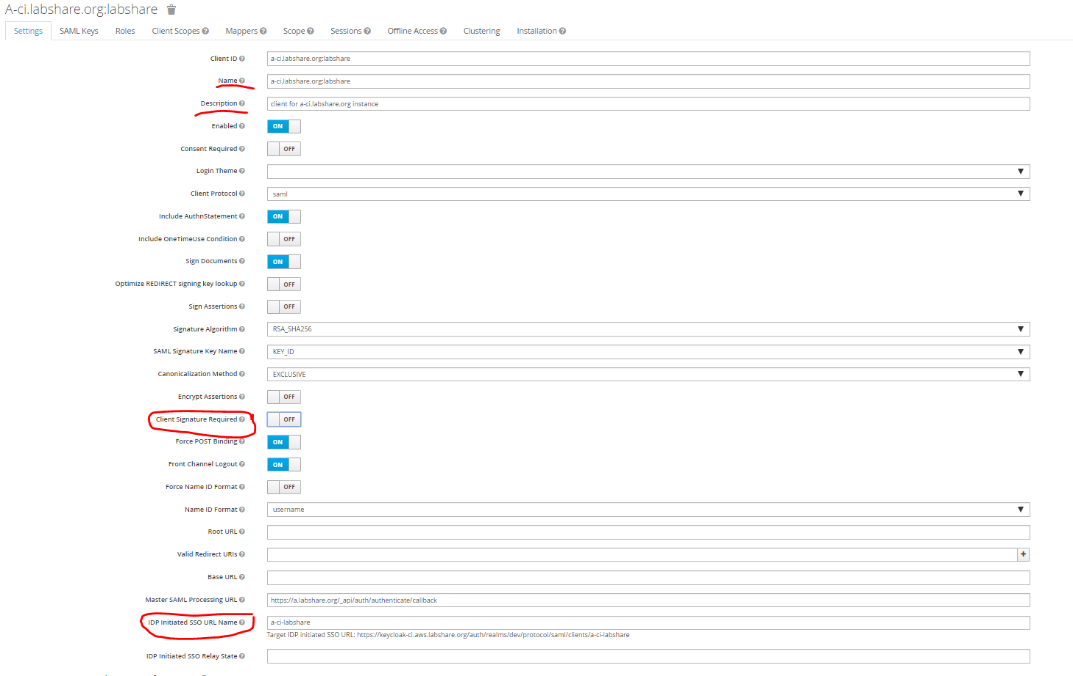
- On the next screen enter Name and Description for the client. Disable “Client Signature Required”. Set a unique string for IDP initiated SSO URL NameID and Save
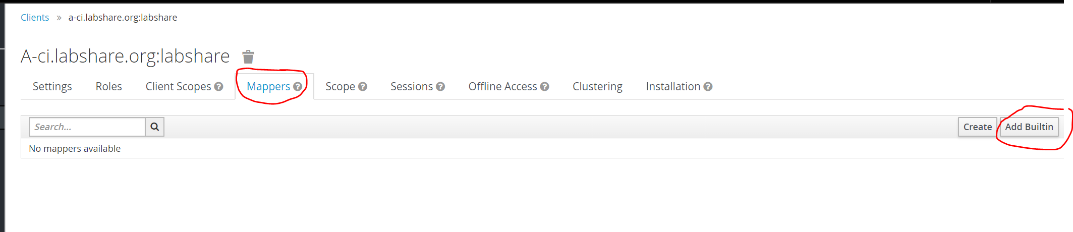
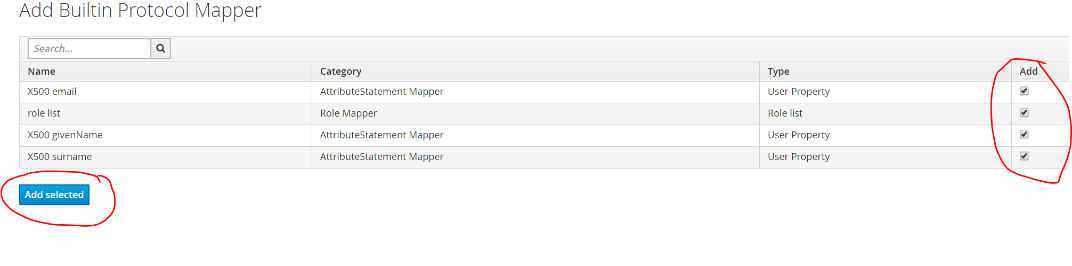
- Map the SAML assertion attributes . Click on the Mappers tab on the top and select “Add Buitin”
- Select ALL and add
-
By default the assertion attributes are in URN format. You can either leave them with defaults Or rename the attributes on Keycloak to be more user friendly. We will leave the defaults for this example.
-
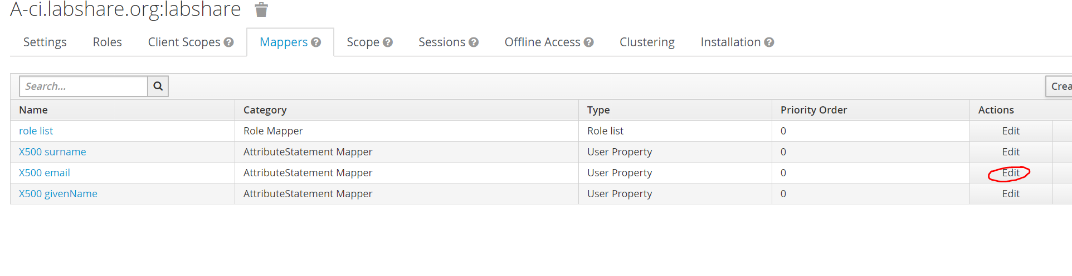
If you want to rename then ,Click on edit beside each attribute and change the SAML attribute name
- Note down the clientID and Save IDP metadata available at
https://{KEYCLOAK-URL}/auth/realms/{REALM-NAME}/protocol/saml/descriptor
(Eg:
https://keycloak-test.aws.labshare.org/auth/realms/test/protocol/saml/descriptor)
Save the X509 certificate to a .cer file and note down the EntityID, SingleSignOnService URL for POST profile and SingleLogoutService URL for POST profile
Create an Identity Provider Configuration in LSAuth
-
Log into the LS Auth console for and select the tenant that you will use.
-
Select “Providers” in the left nav menu and click the “Add New” button.
-
Select Provider Type “SAML2”
-
Enter the below details (You will need to use the details you noted above from IDP metadata )
IDP URL (IDP Login URL): SingleSignOnService URL copied from Keycloak
IDP metadata (Eg:
https://keycloak-ci.aws.labshare.org/auth/realms/dev/protocol/saml)
Logout URL (IDP Logout URL): SingleLogoutService URL copied from
Keycloak IDP metadata (Eg:
https://keycloak-ci.aws.labshare.org/auth/realms/dev/protocol/saml,
Keycloak uses same)
Realm is the Client ID copied from Keycloak IDP configuration
Signing Cert: IDP signing cert copied from Keycloak IDP metadata
- Use “User Profile Script” editor to set claim mappings. Copy the below script into the “User profile Script” block
module.exports = function mapUserProfile(ctx, callback) {
const claims = ctx.secrets.claims;
const profile = {
email: claims["urn:oid:1.2.840.113549.1.9.1"],
given_name: claims["urn:oid:2.5.4.42"],
last_name: claims["urn:oid:2.5.4.4"]
};
callback(null, profile);
}
- Save the provider